General Information - Whitelisting CallTower Accounts
For Calltower to configure services and provide some professional services, we may sometimes require a combination of a service account or a GDAP (Granular Delegated Admin Privileges) relationship. We understand that our customers often have their own security policies in place that may restrict access to only be available in certain scenarios. For us to provide the requested services, we ask that our customers whitelist Calltower IP ranges and partner accounts from those security policies.
Note: All Calltower’s partner accounts used in the GDAP relationship adhere to strict security policies outlined below:
- Passwordless for all accounts, only allowing FIDO keys or MS Authenticator phone sign-in
- Full set of best practice conditional access policies in place
- Only modern authentication clients allowed - all legacy authentication blocked
- Ony Intune-managed compliant devices allowed to access resources
- All accounts and role assignments audited quarterly
Prerequisites:
An admin account within the Microsoft 365 tenant. This admin account needs to have either the Conditional Access Administrator, Security Administrator, or Global Administrator role.
Adjusting Conditional Access Policies
Below are general steps to accomplish this whitelisting by modifying a conditional access policy that grants or blocks access on certain conditions. Remember that the steps may vary depending on your company’s security policies and configurations. If additional help is needed, you can review Microsoft’s documentation here or contact Microsoft support for additional help.
Tip: If you're unsure which conditional access policies to adjust, you may use the "What if" feature to test and see which policies will take effect for our partner accounts. When specifying the Microsoft Entra organization, enter cspcalltower.onmicrosoft.com.


Include Users
This list of users typically includes all the users an organization is targeting in a Conditional Access policy.
The following options are available to include when creating a Conditional Access policy:
- Under “Assignments”, select the option for “Users”.
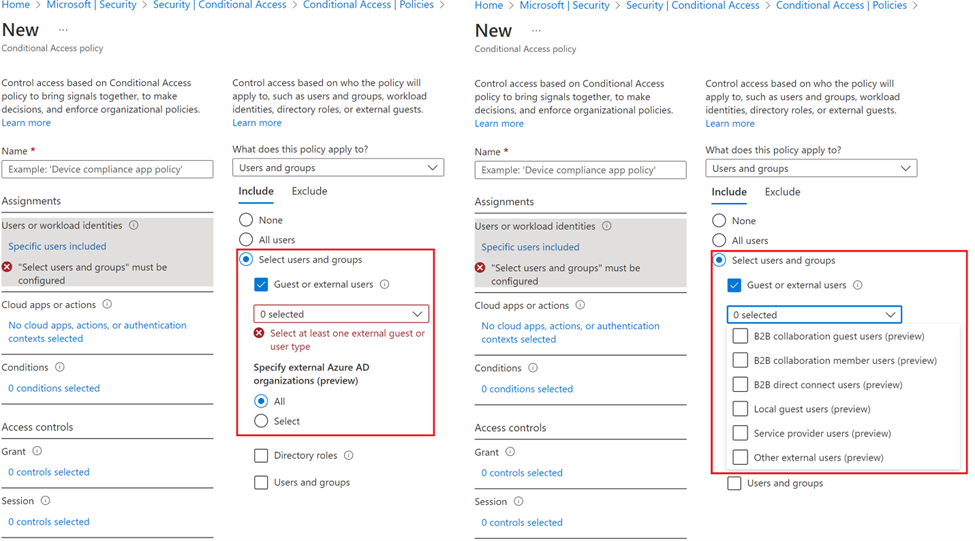
- Select “Users and Groups
- Select “Guest or external users”
- This selection provides several choices that can be used to target Conditional Access policies to specific guest or external user types and specific tenants containing those types of users. There are several different types of guest or external users that can be selected and multiple selections can be made:
- Select “Service provider users” to configure for Calltower CSP users.
- For GCCH customers, select “B2B Collaboration Guest”.
- One or more tenants can be specified for the selected user type(s), or you can specify all tenants. If you chose to specify a single tenant, you can search for the domain name “cspcalltower.onmicrosoft.com”.
- This selection provides several choices that can be used to target Conditional Access policies to specific guest or external user types and specific tenants containing those types of users. There are several different types of guest or external users that can be selected and multiple selections can be made:
- Select “Guest or external users”
External Partner Access
Conditional Access policies that target external users may interfere with service provider access, for example, granular delegated admin privileges. For more information, see Introduction to granular delegated admin privileges (GDAP). For policies that are intended to target service provider tenants, use the Service provider user external user type available in the Guest or external users selection options.
Exclude users
When organizations both include and exclude a user or group, the user or group is excluded from the policy, as an exclude action overrides an include in policy.
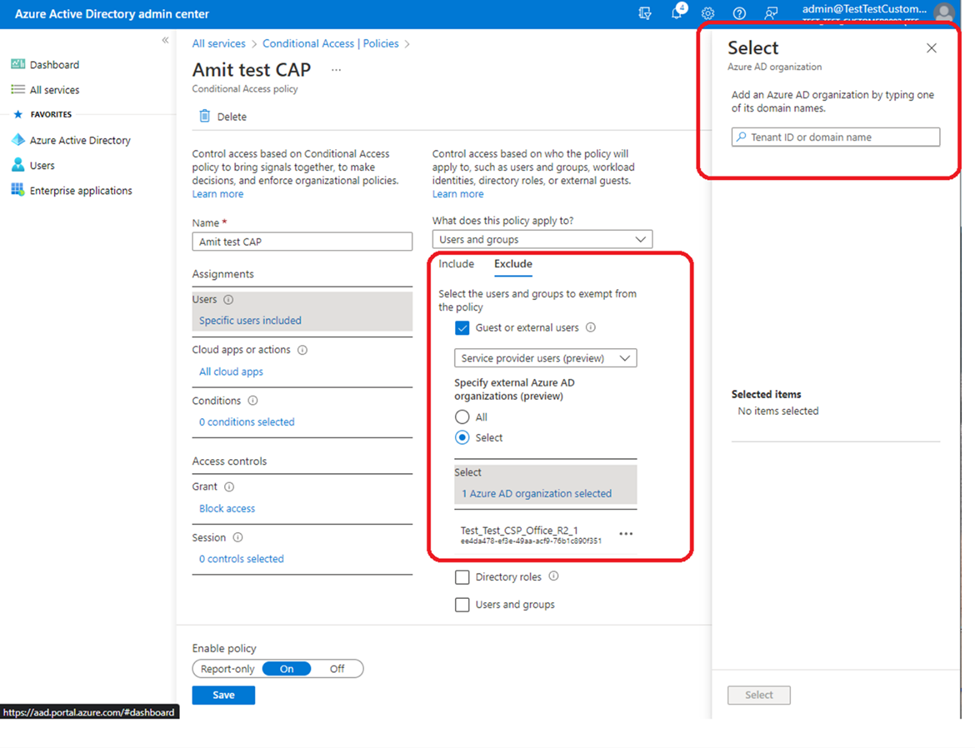
The following options are available to exclude when creating a Conditional Access policy:
- Select “Guest or external users”
- This selection provides several choices that can be used to target Conditional Access policies to specific guest or external user types and specific tenants containing those types of users. There are several different types of guest or external users that can be selected, and multiple selections can be made:
- For commercial customers with a GDAP relationship, select “Service provider users”.
- For GCCH (Government Cloud) customers, select “B2B Collaboration Guest”.
- One or more tenants can be specified for the selected user type(s), or you can specify all tenants. If you chose to specify a single tenant, you can search for the domain name “cspcalltower.onmicrosoft.com”.
- This selection provides several choices that can be used to target Conditional Access policies to specific guest or external user types and specific tenants containing those types of users. There are several different types of guest or external users that can be selected, and multiple selections can be made:
Please note that the steps below are only required if a service account has been requested by Calltower.
Adding A Named Location IP Range
If a service account hasn’t been requested, these steps are not needed.
- Login to https://portal.azure.com
- Navigate to “Microsoft Entra ID”.
- Select “Security” from the left-hand menu.
- Select “Named locations”.
- Towards the top of the page, you will see an option to add “IP ranges location”. Select this option.
- Enter a name, such as “Calltower IPs”.
- Click the “+” to add the first range “69.4.184.0/24” and then click “Add” once entered.
- Repeat step 7 to add the second range “205.196.174.0/24”.
- Click “Create” at the bottom right corner of the page.
Updating conditional access policy to include / exclude the named location above.
- Under the “Conditions” section select “Conditions Selected”.
- Select the option under “Locations”
- Change the “Configure” toggle to “Yes”
- Select the option for “Include” or “Exclude” and then select “Selected locations”.
- Under the “Select” section, add the previously created location with the Calltower IPs.
Configuring cross-tenant access settings
(Not always required)
In some situations you may need to adjust your cross-tenant access settings within Entra ID. This usually won't be needed though unless all other measures have been exhausted.
Information on configuring these settings can be found in the links below.
Cross-tenant access overview - Microsoft Entra External ID | Microsoft Learn
Configure B2B collaboration cross-tenant access - Microsoft Entra External ID | Microsoft Learn
